Ab jetzt bei uns – Microsoft Surface für Ihr Business
Ab sofort sind wir Ihr Microsoft Surface-Partner im Bergischen Land. Egal, mit welchem Gerät Sie heute arbeiten, einen Blick auf das Surface Book und das Surface Pro 4 sollten Sie riskieren – auch auf das Risiko hin, dass Sie dann dringend eines besitzen möchten.
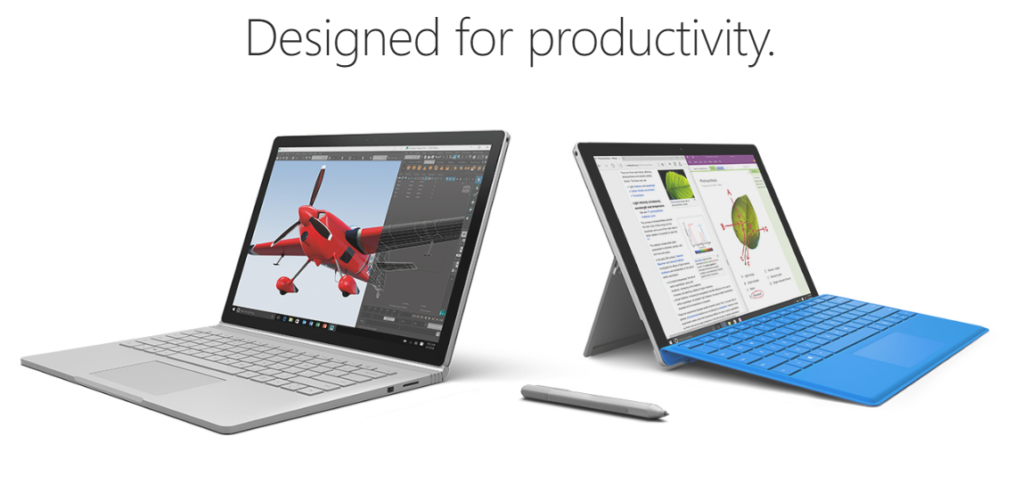
Microsoft stellt mit der Surface Reihe professionelle Arbeitsgeräte mit höchster Flexibilität bereit – egal, ob Sie mit der Tastatur, dem Stift, oder dem Touch-Bildschirm arbeiten möchten. Für den Einsatz im Tagesgeschäft ist es aber sinnvoll, eventuelle Risiken abzusichern und sich die Verfügbarkeit und den Service zu sichern. Hierfür haben wir drei unterschiedliche Service-Pakete für Sie geschnürt:
| BRING or SEND IN |
ON DESK DELIVERY |
FRONT DESK DELIVERY |
|
- Abgabe/Einsendung ins Reperatur-Zentrallager durch den User
- Telefonischer Support bei technischen Problemen inklusive
- RMA Handling inklusive
|
- Tausch des defekten Gerätes durch einen Techniker direkt am Arbeitsplatz
- Telefonischer Support bei technischen Problemen inklusive
- RMA Handling inklusive
|
- Tausch des defekten Gerätes an der Rezeption/ dem Empfang des Users
- Telefonischer Support bei technischen Problemen inklusive
- RMA Handling inklusive
|
| 80 € / pro Jahr |
160 € / pro Jahr |
110 € / pro Jahr |
Lust auf das ultimative Windows-Erlebnis? Dann freuen wir uns auf Ihren Anruf:





