In Zeiten, in denen viele Unternehmen und Mitarbeiter verunsichert sind, oder über Notfallpläne im Falle einer Quarantäne nachdenken, haben wir ein paar Corona-Tipps für Unternehmen zusammengestellt, die das dezentrale Arbeiten vereinfachen und sicher gestalten:
UPDATE 26.03.2020:
Unser Partner G DATA stellt drei kostenfreie Trainings zum Thema „Sicher arbeiten im Home-Office“ bereit. Eine Registrierung ist hier erforderlich.
Die Sorge vor einer Infektion mit dem Corona-Virus wächst und immer mehr Unternehmen lassen ihre Mitarbeiter von zu Hause arbeiten. Häufig nutzen sie dafür ihren privaten PC – ein offenes Tor für Cyberkriminelle, die es auf ihre Firmendaten abgesehen haben.
Dafür stellt G DATA kostenfreie 180-Tage-Lizenzen der G DATA Internet Security für Windows und Mac für Home-Office-User zur Verfügung. Fragen Sie uns nach Ihrer 180-Tage-Lizenz für Ihre Mitarbeiter im Home-Office.
Mit unserem Partner Fortinet ermöglichen wir sichere Verbindungen vom Home-Office in das Unternehmensnetz.
Dabei wird auf dem Notebook des Mitarbeiters der FortiClient als VPN-Software installiert und mit der zentralen FortiGate Firewall des Unternehmens verbunden. Je nach Rechtezuweisung kann der Mitarbeiter damit von zu Hause auf alle ihm erlaubten Ressourcen im Unternehmen zugreifen und somit arbeiten, als wäre er vor Ort. Für gesteigerte Sicherheit sorgt dabei die optionale 2-Faktor-Authentifizierung mittels FortiToken Mobile. Hier wird über eine App auf dem Smartphone des Mitarbeiters ein Einmal-Passwort erzeugt, dass nur für kurze Zeit gültig ist und somit ein hohes Maß an Sicherheit bietet.
Die passenden mobilen Endgeräte stellen wir mit unserem Partner Fujitsu zur Verfügung. Wie in einem aktuellen Fall gezeigt, sind wir momentan auch kurzfristig noch lieferfähig. Dabei stehen neben der Kaufoption auch Leasing, oder Hardware-as-a-Service als Optionen bereit.
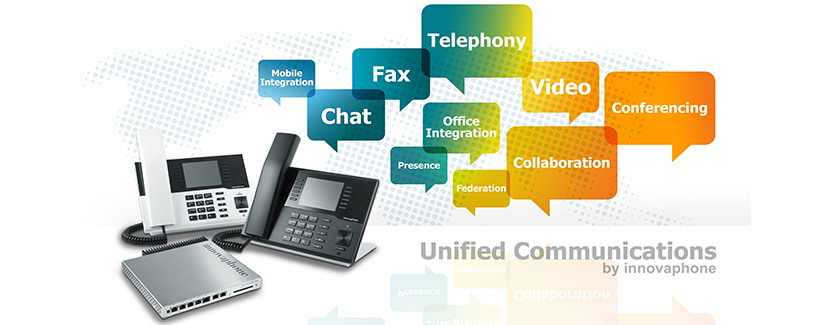
Kommunikation ist jedoch im Normalfall nicht nur auf E-Mails beschränkt, sondern ein vollwertiger mobiler Arbeitsplatz umfasst auch Telefonie, Video, Instant Messaging, Präsenzinformationen u.v.m.
Hierbei unterstützen wir Sie mit unseren Partnern Cisco und Innovaphone.
Dabei ist es egal, ob Sie eine Cloud-Telefonanlage bevorzugen, oder ob Sie Ihre Mitarbeiter an die eigene Anlage im Unternehmen anbinden möchten. Wir haben die passende Lösung, damit auch Ihre mobilen Nutzer, oder Mitarbeiter im Home-Office als ganz normale Teilnehmer Ihrer Anlage auftreten – mit offizieller Firmenrufnummer und interner Durchwahl.
Wenn es darüber hinaus gehend um standortübergreifende Zusammenarbeit geht, ist Cisco Webex eine hervorragende Wahl. Durch die Präsenz in vielen Ländern der Welt ist Cisco Webex eine hervorragende Lösung zur Zusammenarbeit.
Webex kann als Plattform von den allermeisten Endgeräten aus genutzt werden, egal ob Desktop, Notebook, Tablet, oder Smartphone.
AKTUELLE AKTION: Unser Partner Cisco stellt eine zeitlich unbefristete Einzellizenz kostenfrei zur Verfügung.
Bei darüber hinausgehenden Anforderungen kann die Webex-Lösung natürlich auch um Videokonferenzsysteme, oder Smartboards erweitert werden.
Für die Notfallprävention in Sachen Corona, aber auch für ganz einfach mehr Flexibilität und zukunftsfähigeres Arbeiten, bieten wir die unterschiedlichsten Möglichkeiten für Unternehmenskunden an.
Sprechen Sie mit uns und lassen Sie uns gemeinsam das passende Konzept für Ihr Business erarbeiten.