G DATA Exploit-Schutz wehrt effektiv Angriffe durch infizierte Magento-Shops ab
22.10.2015 | Autor: Siebert, Thomas , Christian Lueg
Tausende von Online-Shops, die auf eine veraltete Version der e-Commerce Plattform Magento setzen, wurden laut einem Bericht der Sicherheitsfirma Sucuri (https://blog.sucuri.net/2015/10/massive-magento-guruincsite-infection.html) vom 18.10.2015 mit Schadcode infiziert. Besuchern dieser Webseiten wird ein Exploit-Kit untergeschoben, um Bezahl- oder Login-Daten zu stehlen. Es handelt sich hierbei um die drittgrößte Angriffswelle, die die G DATA Sicherheitsexperten in diesem Jahr registrierten. Die Angriffe dauern allerdings noch an.
Bereits seit dem 17. Oktober 2015, also einen Tag früher, stellen die G DATA SecurityLabs eine steigende Zahl von abgewehrten Infektionsversuchen durch verschiedene Exploit-Kits fest. Der G DATA Exploit-Schutz, der in allen G DATA Sicherheitslösungen integriert ist, schützt Kunden zuverlässig vor den Auswirkungen durch den Schadcode.
Verschiedene Exploit-Kits im Einsatz
Medienberichte, die sich auf einen Beitrag der Firma MalwareBytes (https://blog.malwarebytes.org/exploits-2/2015/10/new-neutrino-ek-campaign-drops-andromeda/) berufen, berichten ausschließlich von Angriffen über das Neutrino Exploit-Kit. Die G DATA SecurityLabs stellen allerdings bereits ab dem 17.10. eine erhöhte Anzahl von abgewehrten Angriffen der Exploit-Kits Nuclear und Angler fest. Die Angriffe über Nuclear fanden ausschließlich am 17.10. statt, während die Angriffe über Angler erst im Laufe des 18.10. abebbten. Am gleichen Tag begann eine massive Infektionswelle durch das Neutrino Exploit-Kit, welche weiterhin anhält.
Wie kommt der Schadcode auf die Webseiten?
Der Hersteller der Onlineshop-Software geht von veralteten Versionen aus, die von Betreibern weiterhin eingesetzt werden. Angreifer missbrauchen bekannte – aber in den alten Versionen noch nicht geschlossene – Sicherheitslücken, um die Shops mit dem Schadcode zu infizieren. Betreiber, die hiervon betroffen sind, sollten ihr Shopsystem umgehend aktualisieren.
Was ist ein Exploit-Kit?
Ein Exploit-Kit ist ein Tool das, je nach Ausführung, eine Vielzahl von unterschiedlichen Angriffen auf Schwachstellen (Exploits) enthält. Besucht ein Nutzer eine manipulierte Webseite, wie im aktuellen Fall die Shops mit einem Magento-System, wird mit Hilfe des Exploit-Kits die Konfiguration des PCs auf Sicherheitslücken in Anwendungen hin überprüft (Browser, installierte Software oder Betriebssystem). Findet sich auf dem System eine Schwachstelle oder gar mehrere, wird ein passender Exploit an den Client gesendet, der die gefundene Sicherheitslücke ausnutzt, um danach unbemerkt weiteren Schadcode auf den angreifbaren Rechner zu laden (Drive-by-Infektion).
G DATA Exploit-Schutz überprüft das System auf seltsames Verhalten
Das Ausnutzen von Software-Sicherheitslücken durch sogenannte Exploits ist für Cyberkriminelle mittlerweile die beliebteste Methode, um Computer mit Schadcode zu infizieren. Schadsoftware wird heute vor allem über Internetseiten, die von Cyber-Kriminellen manipuliert wurden, verbreitet. – Die Seiten-Betreiber ahnen davon meist nichts. Exploits suchen dabei gezielt nach Schwachstellen im System des Anwenders.
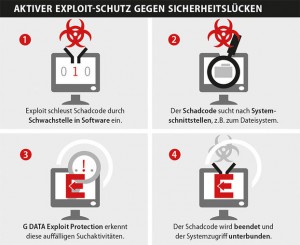
Mit G DATA wird das Ausnutzen einer Sicherheitslücke effektiv geblockt und das Ausführen der Schadcode-Infektion verhindert. Der Exploit-Schutz von G DATA überprüft das Verhalten der installierten Programme permanent auf Unregelmäßigkeiten. Wird ungewöhnliches Verhalten im Programmablauf festgestellt, blockiert die G DATA Sicherheitslösung den Angriffsversuch, stoppt den Eindringling und schlägt umgehend Alarm. Selbst vor bisher unbekannten Angriffen, sogenannten „Zero-Day-Exploits“, schützt der G DATA Exploit-Schutz.
[1] http://magento.com/security/news/important-security-update
G DATA Software AG – Lesen Sie mehr auf:
https://blog.gdata.de/artikel/g-data-exploit-schutz-wehrt-effektiv-angriffe-durch-infizierte-magento-shops-ab/
G DATA Lösungen erhalten Sie bei Ihrem G DATA Partner Oberberg-Online.


